Outlook Web Application under attack
Malware targeting Microsoft Outlook Web App is after your password
A newly discovered malware targets Microsoft’s Outlook Web App, the company’s web-based email client. The news was unveiled by security firm Cybereason, which said the advanced persistent threat (APT) can enable patient attackers to steal an organization’s email passwords over time.
App, the company’s web-based email client. The news was unveiled by security firm Cybereason, which said the advanced persistent threat (APT) can enable patient attackers to steal an organization’s email passwords over time.
By using this approach, the hackers managed to collect and retain ownership over a large set of credentials, allowing them to maintain persistent control over the organization’s environment, Cybereason says.
The company found the malware after an organization’s IT team spotted “behavioral abnormalities” in its email servers.
The security firm goes on explaining the malware: “The Cybereason platform found a suspicious DLL loaded into the Outlook Web App (OWA) server (a webmail component of Microsoft Exchange Server), with several interesting characteristics. Although it had the same name as another benign DLL, the suspicious DLL went unsigned and was loaded from a different directory. Since OWA servers typically load only legitimately signed DLLs, the Cybereason behavioural engine immediately elevated this event to a suspicion”.
Cybereason says the attack is important, as whoever has access to the OWA server, owns the organization’s domain credentials:
“The attack on OWA is significant”, claims Cybereason, because OWA authentication is based on domain credentials. “Whoever gains access to the OWA server becomes the owner of the entire organisation’s domain credentials”, it says.
“The hackers installed a back-doored malicious OWAAUTH.DLL which was used by OWA as part of the authentication mechanism, and was responsible for authenticating users against the Active Directory (A/D) server used in the environment. In addition, the malicious OWAAUTH.DLL also installed an ISAPI filter into the IIS server, and was filtering HTTP requests”.
“This enabled the hackers to get all requests in cleartext after SSL/TLS decryption. The malware replaced the OWAAUTH by installing an IIS filter in the registry, which enabled the malware to automatically load and persist on every subsequent server restart”, adds Cybereason.
Synaptics’ Clearforce technology to bring 3D Touch-style screens to Android
Welcome to WordPress. This is your first post. Edit or delete it, then start blogging!
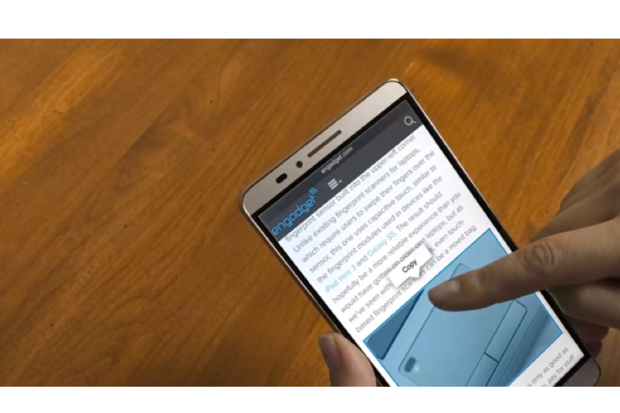
A pressure-sensitive display will open up another layer of interaction beyond the usual staple of touches and swipes.
Your next Android phone’s screen might be more like a giant pressure-sensitive button.
That’s because Synaptics is pushing a new capability for smartphones called ClearForce. Much like Apple’s 3D Touch, you’ll be able to “press” on the screen and get a popup menu or another type of contextual action.
This would allow for different types of interaction with your screen beyond the standard touch, press-and-hold, or pinch-to-zoom. Synaptics is a big player with touch sensors. By backing new tech like this, there’s a good chance you’ll start to see it in a bunch of new phones over the coming year.
However, Synaptics is at work on more than just menus. Synaptics says the new sensor technology will allow for variable speed scrolling, new ways to pan and zoom over pictures, and additional contextual menus depending on how much pressure is applied to the screen.
This isn’t the first time a pressure-sensitive screen has popped up in the world of Android. The Huawei Mate S screen can be hard pressed to zoom in to particular parts of an image or even act as a scale.