https://www.youtube.com/watch?v=W7U2u-qLAB8 Honeypots were all the rage in the 90’s – A raft of tools (and even a world-wide alliance) sprung up extolling their virtues but they never managed to live up to their hype. They were largely relegated to researchers and tinkerers on the fringes. At the same time, we have the Verizon DBIR telling us that most companies are first informed by 3rd parties that they are breached. This is a stupid situation to be in. Well deployed honeypots can be invaluable tools in the defenders arsenal, and don’t need to look anything like the honeypots of old. From application layer man-traps, to booby-trapped documents. From network-level deception, to cloud based honeypottery, we are bringing honeypots back! During this talk, we will discuss and demonstrate the current state of the art regarding honeypots. We will explore the factors that limit adoption (and will discuss how to overcome them.) We will demonstrate new techniques to make your honeypots more “hacker-discoverable” & will share data from running actual honeypots in real organizations. We will also discuss (and release) OpenCanary, our new open source honeypot (along with supporting scripts and utilities). Over the past few years, honeypots have gotten a bit of a bad rap. We will give you tools, techniques and takeaways, to move them from geeky time-wasters, to the most useful pieces of kit you will deploy.
Tag Archives: Computer
Adobe Releases Lightroom Fix
In a quick turnaround, Adobe patched a bug causing its Lightroom program to crash after a software update.
“I’d like to personally apologize for the quality of the Lightroom 6.2 release we shipped on Monday”, stated Adobe Product Management Photography Director Tom Hogarty on the company’s official blog this past Friday, “in our efforts to simplify the import experience we introduced instability that resulted in a significant crashing bug”. However, the apology wasn’t met with enthusiasm, as the bug-fixing patch also eliminated some desired features of the program. The update, aside from improving the import process, was intended to enhance several other features of the program including improving haze elimination. It was originally intended to simplify and streamline the program, however this may have been overdone, according to rising user responses expressing discontent with the deleted features.
Hogarty explained that Lightbox’s very birth was based on an open dialogue with photographers and artists who would be most interested in the program, and that a breach of such communication as with these past several updates created many of the issues Adobe is now dealing with. Historically, Adobe has been very responsive with patches, however users have been frustrated in the past with a lack of compensation (such as the ability to back out of a long Adobe Creative Cloud contract), or as with this case, a bug fix which also carries undesirable results with it, which Hogarty addressed with his explanation that “we removed some of our very low usage features to further reduce complexity and improve quality”. Whether or not those features were indeed ‘low usage’ is coming to the surface after a weekend with the new update.
Outlook Web Application under attack
Malware targeting Microsoft Outlook Web App is after your password
A newly discovered malware targets Microsoft’s Outlook Web App, the company’s web-based email client. The news was unveiled by security firm Cybereason, which said the advanced persistent threat (APT) can enable patient attackers to steal an organization’s email passwords over time.
App, the company’s web-based email client. The news was unveiled by security firm Cybereason, which said the advanced persistent threat (APT) can enable patient attackers to steal an organization’s email passwords over time.
By using this approach, the hackers managed to collect and retain ownership over a large set of credentials, allowing them to maintain persistent control over the organization’s environment, Cybereason says.
The company found the malware after an organization’s IT team spotted “behavioral abnormalities” in its email servers.
The security firm goes on explaining the malware: “The Cybereason platform found a suspicious DLL loaded into the Outlook Web App (OWA) server (a webmail component of Microsoft Exchange Server), with several interesting characteristics. Although it had the same name as another benign DLL, the suspicious DLL went unsigned and was loaded from a different directory. Since OWA servers typically load only legitimately signed DLLs, the Cybereason behavioural engine immediately elevated this event to a suspicion”.
Cybereason says the attack is important, as whoever has access to the OWA server, owns the organization’s domain credentials:
“The attack on OWA is significant”, claims Cybereason, because OWA authentication is based on domain credentials. “Whoever gains access to the OWA server becomes the owner of the entire organisation’s domain credentials”, it says.
“The hackers installed a back-doored malicious OWAAUTH.DLL which was used by OWA as part of the authentication mechanism, and was responsible for authenticating users against the Active Directory (A/D) server used in the environment. In addition, the malicious OWAAUTH.DLL also installed an ISAPI filter into the IIS server, and was filtering HTTP requests”.
“This enabled the hackers to get all requests in cleartext after SSL/TLS decryption. The malware replaced the OWAAUTH by installing an IIS filter in the registry, which enabled the malware to automatically load and persist on every subsequent server restart”, adds Cybereason.
Synaptics’ Clearforce technology to bring 3D Touch-style screens to Android
Welcome to WordPress. This is your first post. Edit or delete it, then start blogging!
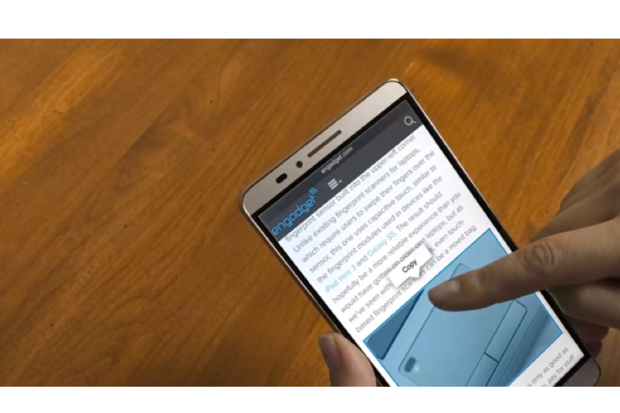
A pressure-sensitive display will open up another layer of interaction beyond the usual staple of touches and swipes.
Your next Android phone’s screen might be more like a giant pressure-sensitive button.
That’s because Synaptics is pushing a new capability for smartphones called ClearForce. Much like Apple’s 3D Touch, you’ll be able to “press” on the screen and get a popup menu or another type of contextual action.
This would allow for different types of interaction with your screen beyond the standard touch, press-and-hold, or pinch-to-zoom. Synaptics is a big player with touch sensors. By backing new tech like this, there’s a good chance you’ll start to see it in a bunch of new phones over the coming year.
However, Synaptics is at work on more than just menus. Synaptics says the new sensor technology will allow for variable speed scrolling, new ways to pan and zoom over pictures, and additional contextual menus depending on how much pressure is applied to the screen.
This isn’t the first time a pressure-sensitive screen has popped up in the world of Android. The Huawei Mate S screen can be hard pressed to zoom in to particular parts of an image or even act as a scale.